- Odyssey Platform Weekly
- Posts
- Odyssey Platform # 06
Odyssey Platform # 06
Another exciting week in the Platform Engineering ecosystem!
Editor's Note
Welcome to another edition of Odyssey Platform Weekly! This week, we’re diving into fresh insights, key events, and powerful stories shaping the future of platform engineering.🗞️ In this newsletter
🗓️ Events
🔦 Tool Spotlight
Vanta is a leading trust management platform that automates compliance processes for frameworks like SOC 2, ISO 27001, HIPAA, and GDPR, enabling businesses to achieve and maintain security certifications efficiently.
🔍️ Deep Dive
Discover how HashiCorp Vault securely connects secrets, policies, and principals—enabling your Kubernetes workloads to authenticate, authorize, and fetch secrets without ever hardcoding credentials. Learn how Vault’s elegant trinity unlocks zero-trust secret management for modern apps.
🎯 Stay Inspired - Case Studies
👀 In Case you missed it
Latest news & events in the platform engineering domain
📆 Upcoming Events
🧠 Kubeflow Virtual Planning Symposium 2025
📅 Jul 9-10, 2025 – Virtual
The Kubeflow Virtual Planning Symposium 2025 is the must-attend event for shaping the future of GenAI and MLOps in the cloud-native ecosystem. 🔥
👉 Register here

🔦 Tool Spotlight
Vanta is a leading trust management platform that automates compliance for frameworks like SOC 2, ISO 27001, HIPAA, PCI, and GDPR. By integrating with over 300 tools, it continuously monitors security controls, automates evidence collection, and simplifies audits—reducing compliance prep time by up to 50%.
Its AI-powered features, including the Vanta AI Agent, streamline tasks like security questionnaires and risk assessments, making compliance faster and more efficient.
Trusted by over 8,000 companies worldwide, Vanta helps organizations build and maintain customer trust through real-time security visibility and automated compliance workflows.
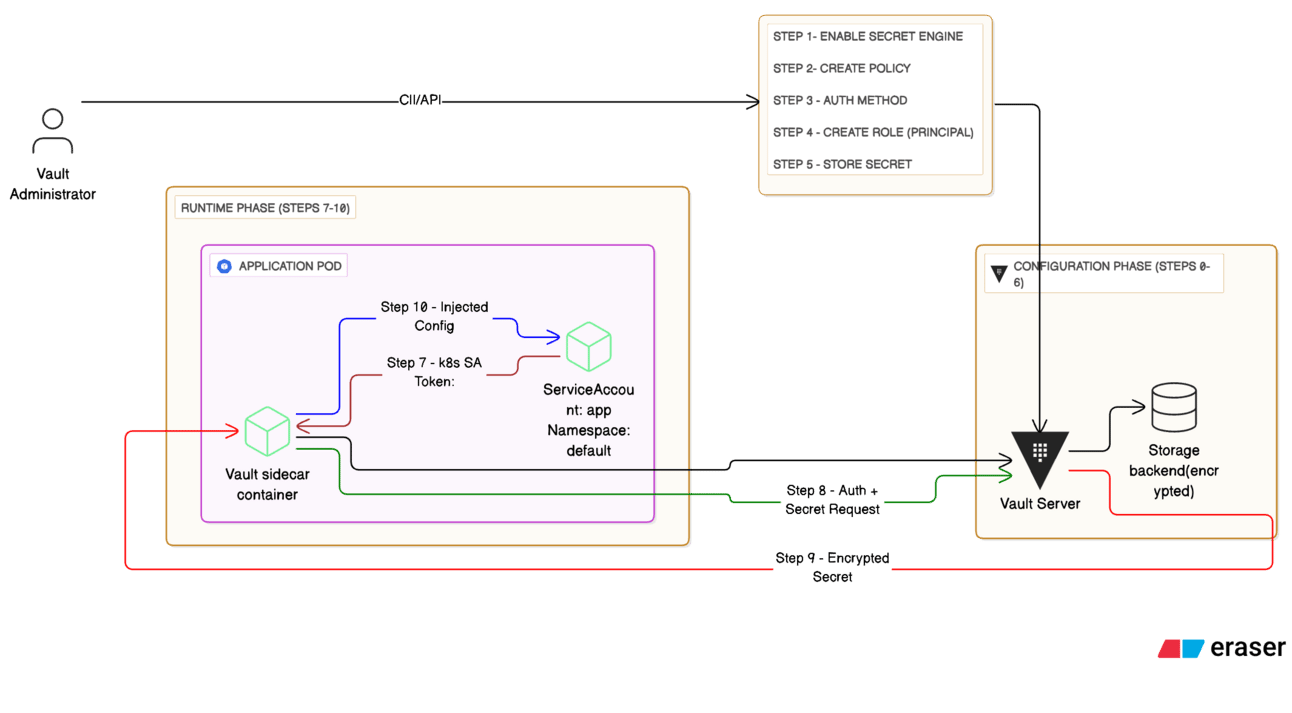
🚀 Demystifying HashiCorp Vault: The Secret, Policy & Principal Trinity
Ever wondered how HashiCorp Vault transforms chaos into secure, organized secret management? Welcome to the elegant world of Vault's core trinity!
In this deep dive, we explore the foundational dance of Secrets, Policies, and Principals!
Secret Engine ↔ Policy ↔ Principal
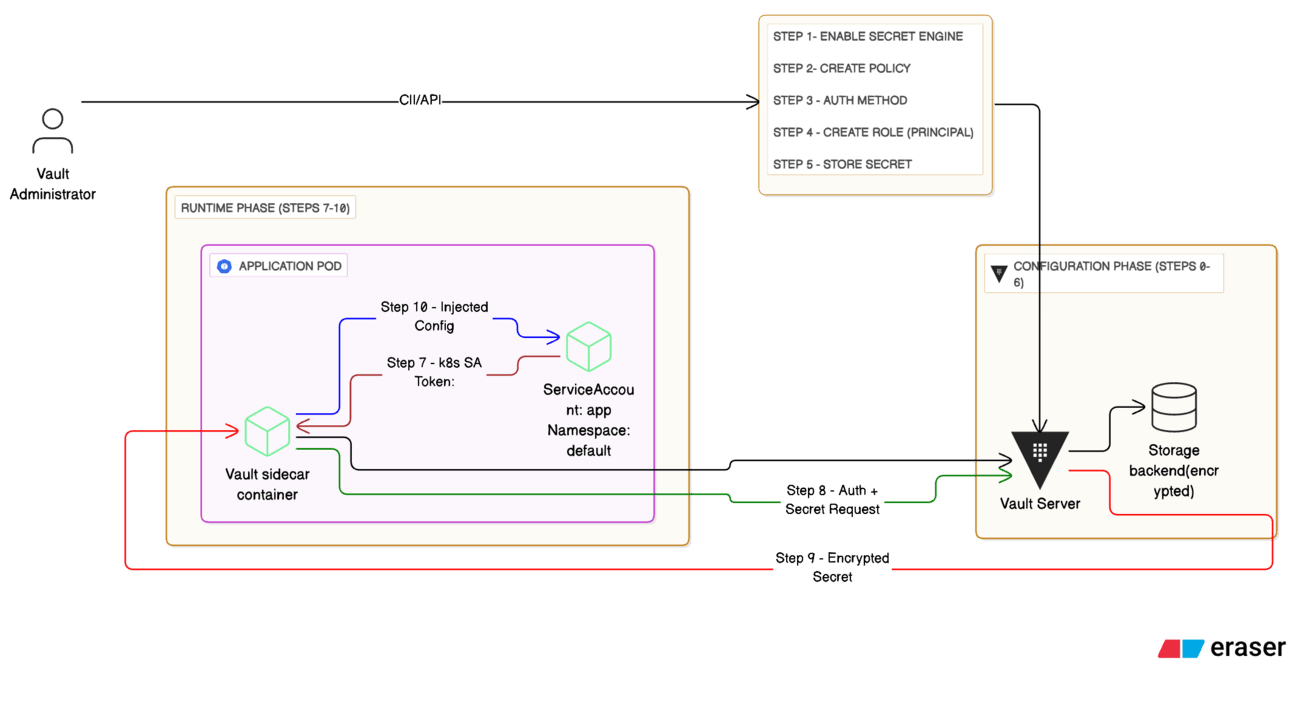
HashiCorp Vault Flow
🎬 Act 1: The Foundation - Secret Engines
When Vault starts its journey, the first magical step is creating a engine for your secrets. Think of this as building the vault's rooms! 🏗️
vault secrets enable -path=kv kv-v2What just happened?
Created a KV (Key-Value) version 2 secret engine
Established the path /kv/ as your secret path
Enabled versioning and metadata for all secrets stored here
This is like getting the keys to a brand new, high-security building with infinite rooms! 🔑
🎪 Act 2: The Rulebook - Policies
Here's where Vault shows its true intelligence. Before anyone can access anything, we need rules - and Vault policies are beautifully expressive:
# Save this as app-policy.hcl
path "kv/data/app/*" {
capabilities = ["read", "list"]
}
path "kv/metadata/app/*" {
capabilities = ["read", "list"]
}vault policy write app-policy app-policy.hcl🎯 Policy Anatomy:
Path: Defines WHERE the rule applies (kv/data/app/*)
Capabilities: Defines WHAT actions are allowed (read, list, create, update, delete)
Wildcards: The * means "anything under this path"
👮♂️🏠 Building Access Control: Think of policies as the smart card access rules for a high-security building - they define which floors you can visit, which doors will open for you, and what you can do once inside!
🔄 Act 3: The Identity Bridge - Authentication Methods
But wait - how does Vault know WHO is asking for access? Enter authentication methods:
vault auth enable kubernetesThis magical command opens a communication channel between Vault and Kubernetes. It's like installing a special phone line that only speaks "Kubernetes language"! 📞
Popular Auth Methods:
Kubernetes: For container workloads
AWS IAM: For AWS resources
Azure: For Azure resources
LDAP/AD: For enterprise users
JWT/OIDC: For modern identity providers
🎁 Act 4: The Principal Creation - Roles
Now comes the elegant part - creating roles (principals) that map external identities to internal policies:
vault write auth/kubernetes/role/app \
bound_service_account_names=app \
bound_service_account_namespaces=default \
policies=app-policy \
ttl=1h \
max_ttl=4h🔗 Role Binding Magic:
bound_service_account_names: Which K8s service account can use this role
bound_service_account_namespaces: Which K8s namespace they must be in
policies: Which Vault policies they get (remember our app-policy?)
ttl/max_ttl: How long their access token lasts
This is like creating a pass that says: "If you're the 'app' service account from the 'default' namespace, you get app-policy permissions for 1 hour!" 🎫
🏁 Act 5: The Secret Storage
Finally, let's store some actual secrets:
vault kv put kv/app/config \
db_password=supersecret123 \
api_key=abc-def-ghi-jkl \
redis_url=redis://localhost:6379
Behind the scenes:
Data encrypted with AES-256-GCM
Stored with automatic versioning
Metadata tracked separately
Audit logs capture all access
🚀 The Complete Access Flow
When your application needs secrets, here's the beautiful choreography:
Step 1: The Authentication Dance 💃
# Your pod automatically has this token
cat /var/run/secrets/kubernetes.io/serviceaccount/tokenStep 2: The Vault Login 🎪
vault write auth/kubernetes/login \
role=app \
jwt=<kubernetes_service_account_token>Vault responds with: "Welcome! Here's your temporary access token."
Step 3: The Secret Retrieval 🎁
vault kv get kv/app/configVault checks:
✅ Is your token valid?
✅ Does the app-policy allow reading kv/data/app/*?
✅ Return the encrypted secret, decrypted just for you!
🔧 Real-World Implementation
Here's how it looks in practice with Vault Agent as a sidecar:
# vault-agent-config.hcl
vault {
address = "https://vault.example.com:8200"
}
auto_auth {
method "kubernetes" {
mount_path = "auth/kubernetes"
config = {
role = "app"
}
}
}
template {
source = "/vault/secrets/app-config.tpl"
destination = "/vault/secrets/app-config.json"
}<!-- app-config.tpl -->
{
"database": {
"password": "{{ with secret "kv/app/config" }}{{ .Data.data.db_password }}{{ end }}"
},
"api_key": "{{ with secret "kv/app/config" }}{{ .Data.data.api_key }}{{ end }}"
}💡 Why This Trinity Matters
🔒 Security Win: Secrets never touch your container images or git repos
⚡ Ops Win: Centralized secret management with audit trails
🎯 Dev Win: Applications get secrets automatically without hardcoding
🌟 Advanced Patterns:
Dynamic Secrets: Vault can generate database credentials on-demand
Secret Rotation: Automatic rotation of long-lived secrets
Transit Encryption: Vault as encryption-as-a-service
Certificate Management: PKI secret engine for TLS certificates
🎪 Pro Tips for Vault Mastery:
Start with simple KV secrets, then explore dynamic secrets
Use the principle of least privilege in policies
Implement secret rotation from day one
Monitor and audit all secret access
Use Vault Agent for seamless application integration
🎯 Stay Inspired - Case Studies
Macquarie Bank’s next-generation Cloud Control Plane
Macquarie shares a 3-part deep dive into how they built their next-generation Cloud Control Plane—an internal developer platform that balances golden paths with governance, enabling scalable cloud self-service.
Why Macquarie needed a new control plane and how platform engineering became the foundation for scale, control, and speed.
Part 2: Workflow Bots & Golden Paths
A look at how Argo Workflows and bot-driven automation helped create structured and repeatable golden paths for developers.Part 3: Streamlining the Developer Experience
The final build: How Macquarie aligned tooling, user journeys, and governance guardrails to ship a polished platform experience.
👀 In Case You Missed It…
93% of teams report using GitOps practices, but only 35% have adopted advanced features like continuous reconciliation and auto-rollbacks. The survey shows growing interest, but maturity levels still vary widely.
The Gemini CLI is a new open-source tool built on Google's Gemini 1.5 Pro that brings AI-powered automation to the terminal. Unlike traditional CLI tools, it runs multi-turn conversations, reads local context, and executes shell commands safely within your environment. Designed to simplify DevOps workflows, it supports plugin-based extensibility, offline use, and audit logs—making it a powerful AI copilot for engineers who live in the terminal.
GitLab has rolled out major updates to its CI/CD platform, introducing unified pipeline execution across hybrid and multi-cloud environments. This enhancement allows jobs to run seamlessly across GitLab-hosted and self-managed runners, improving flexibility for regulated industries and distributed teams. The update also includes stronger security posture management, pipeline catalog enhancements, and tighter integration with GitLab Duo, its AI-powered assistant for DevSecOps workflows.
Till next time,